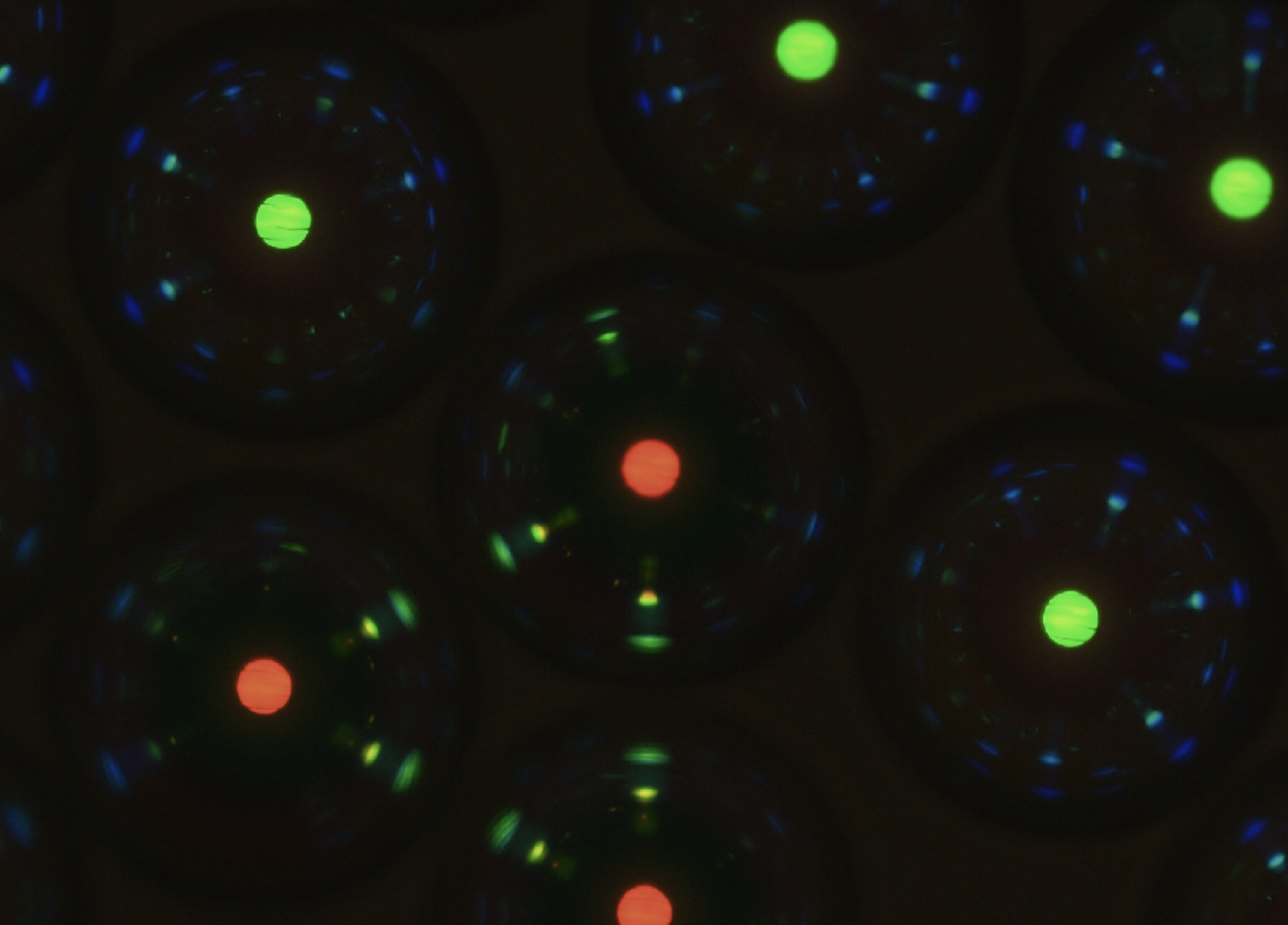



Trace Crystal provides a means of incorporating a unique, uncloneable and untransferable fingerprint directly onto the surface of any solid physical product, to reestablish trust in authenticity and quality. The fingerprint is created by Cholesteric Spherical Reflectors, or CSRs, minuscule spheres with spectacular optical properties invented by our team. By design, the deposition of CSRs into a fingerprint—which we call a CaeSaR tag—leaves the distribution of CSRs random, in a way that not even we can make a copy. The CSRs communicate optically with each other in a complex fashion, in different colors and in different places and directions depending on how the CaeSaR tag is illuminated and viewed. This generates a series of patterns that are unique to each CaeSaR tag. By reading these patterns with a simple optical read-out device, Trace Crystal can verify whether an item is original or fake with great certainty.

Why can you trust CaeSaR tags? A golden rule in cybersecurity for trustworthy authentication is that the algorithm is public but the key is private. Trace Crystal employs the same mindset in the physical domain: the core of our technology is published in the leading scientific journals for anyone to read and be convinced by its reliability. What we do not reveal is our key, i.e., how we implement the technology. You can read a popular science account of how our technology works here. If you wish to see a list of scientific publications describing our technology, click the icon below.
